Monthly Archives: January 2013
Moving SSRS Reports
Yesterday I was tasked with migrating our Citrix EdgeSight database off of a 2005 SQL Server and migrating it to a new 2008R2 Server. No problem, I have done that a million times before. But wait a minute, that database has SSRS reports installed on that server and not our main reporting server. If you follow my blog, you will probably see that I have not had much experience with SSRS, my reporting experience has been with Crystal and other minor packages.
I started researching how to migrate these reports and was not pleased to see Citrix’s response. They recommended migrating the ReportServer and ReportServerTempDB databases to the new server and then reinstalling SSRS on the original server. So what happens then if you have other jobs on the new and old servers? This is not a good recommendation. After an exhaustive search the only option I saw within the tool was to download reports one at a time and upload them into the new server. This was also not an option with a fair amount of reports to migrate.
 Enter Reporting Services Scripter from SQLdbatips.com. Run the program on the original server and select your Report folder and scripts are generated and placed into a folder of your choosing. These scripts can then be copied over to the new server and executed by command shell. In this particular instance we had to reopen the data source and enter new credentials. Problem solved, reports migrated successfully.
Enter Reporting Services Scripter from SQLdbatips.com. Run the program on the original server and select your Report folder and scripts are generated and placed into a folder of your choosing. These scripts can then be copied over to the new server and executed by command shell. In this particular instance we had to reopen the data source and enter new credentials. Problem solved, reports migrated successfully.
Enjoy!
SQL Saturday Updates
 It is an honor and privilege to be selected to present at SQL Saturday Tampa on March 2, 2013. We will be at a new location this year, Hillsborough Community College in beautiful Ybor City, due to our growth over the last couple of years. In addition, we have three pre-cons this year and I will be attending the “Creating Your Best Technical Presentation: A Speaker Workshop” by Buck Woody (b|t). Hopefully, after this session, my presentation skills will continue to improve before my session on that Saturday. If the winter blues got you down then head down to beautiful Tampa for a warm weekend of SQL learning and register for SQL Saturday #192.
It is an honor and privilege to be selected to present at SQL Saturday Tampa on March 2, 2013. We will be at a new location this year, Hillsborough Community College in beautiful Ybor City, due to our growth over the last couple of years. In addition, we have three pre-cons this year and I will be attending the “Creating Your Best Technical Presentation: A Speaker Workshop” by Buck Woody (b|t). Hopefully, after this session, my presentation skills will continue to improve before my session on that Saturday. If the winter blues got you down then head down to beautiful Tampa for a warm weekend of SQL learning and register for SQL Saturday #192.
This year I will finally get to attend two other SQL Saturdays that are in the relative vicinities. In the past there was always something going on during those two weekends. As it stands, I am planning on submitting my newest session, Backups: Getting the Most Out of Your Storage, to both of those events. Curious as to what they are?
SQL Saturday Jacksonville (#SQLSat215) will be April 27th and SQL Saturday Atlanta is tentatively scheduled for May 18th. Come on out and join me at all three of those events and maybe one of them will have some SQLKaraoke for the after event! Enjoy!
SQL Server Auditing: A Learning Series Part Nine, Reporting
Continuing our learning series on auditing, today we look at the next logical step: Reporting. We have created audits for the server and for the database as well as being able to query the audits, but what good is an audit if you cannot print a report and hand it to the auditors?
Having been a developer and admin in my past life, you may find it strange that I have never before today created a SQL Server Reporting Services report. Now don’t get me wrong, I have written a boat load of reports in many other formats (crystal, web, actuate, etc) but have never really had the opportunity or the pleasure to write in my preferred environment.
Given the following function, I thought reporting would be a little more difficult:
SELECT * FROM fn_get_audit_file (‘g:\auditing\*’, DEFAULT, DEFAULT)
This arguments for this function are (file_pattern, initial_file_name, audit_file_offset). The file_pattern argument must include a path and a filename but can include a wildcard. The initial_file_name argument must specify the path and name of a specific file in the file set to start reading the records from or the DEFAULT|NULL value. The audit_file_offset argument will beginning reading the first record after the specified offset (which is a field that can be queried with the function).
Now on to the report….
- Open Visual Studio and choose File –> New Project.
- Select Report Server Project Wizard and name the project appropriately.
- Enter your connection information and credentials.
- When prompted to design the query enter the query above as shown in Figure 1.
- Select additional reporting options as your preferences allow and then save the report.
This concludes our series on auditing, I hope you found it helpful!
SQL Server Auditing: A Learning Series Part Nine
Continuing our learning series on auditing, today we prepare for a database audit. Just like with the server audit specification, you must setup a new server audit that correlates to this database audit specification (remember, it is a one-to-one relationship).
- Create a new server audit for your database audit as demonstrated in part three of this series.
- In SQL Server Management Studio, select the database for which you plan to audit.
- Then select the Security node followed by right-clicking on Database Audit Specification and select New Database Audit Specification.
- From here, the directions are the same as was demonstrated in part five of this series except here we can select the Object Class of either DATABASE, OBJECT, or SCHEMA. For example if we audit the UPDATE action then we can choose the object upon to audit.
Enjoy and stay tuned.
SQL Server Auditing: A Learning Series Part Eight
Continuing our learning series on auditing, today we discuss a couple of caveats to close out the week before we create database audits next week.
- In order to CREATE, ALTER, or DROP on either the server audit or server audit specification, the security principle must be assigned to ALTER ANY SERVER AUDIT or CONTROL SERVER permission.
- You can rename an Audit but not a server audit specification so choose your name wisely.
- In order to modify the properties of either the server audit or server audit specification, you must disable them and then re-enable them after your changes are completed.
- In order to CREATE, ALTER, or DROP a database audit specification, the security principle must be assigned to ALTER ANY DATABASE AUDIT or the ALTER or CONTROL permission on the respective database as well as having the permission in order to connect to the database.
Enjoy and stay tuned as we continue the series next week!
SQL Server Auditing: A Learning Series Part Seven
Continuing our learning series on auditing, today we look at how to query the audit information from the server.
- sys,server_audits displays information on the audits setup on the server.
- sys.server_audit_specifications displays information on the audit specification setup on the server.
- sys.server_audit_specification_details display detailed information about the specifications.
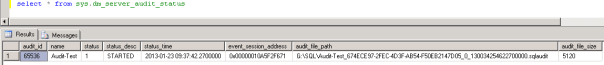
- sys.dm_server_audit_status displays information about the status of your audits.
Enjoy and stay tuned!
SQL Server Auditing: A Learning Series Part Six
Continuing our learning series on auditing, today we look at the results from the audit specification that we created yesterday. In this audit specification we are monitoring for database ownership change or permission change. I changed the owner on one of the databases on the server and an audit log entry was generated as shown in Figure 1. We can see who changed the ownership and what it was changed to. I think it would be better to show me what the original value was. Enjoy and stay tuned!
SQL Server Auditing: A Learning Series Part Five
Continuing our learning series on auditing, today we create a new audit specification (as explained in last week’s post). Remember, in order to create a new server audit specification, you must have created a new server audit. This is a one-to-one relationship and in order to actually collect auditing information both objects are required.
Think of it like an order table that has to have an order lines table in order for a sales order to be made, if that helps your understanding.
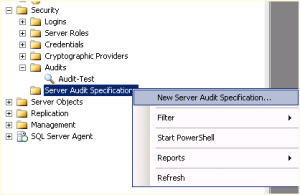
- In the security node of SQL Server Management Studio, right-click on Server Audit Specification and select New Server Audit Specification, as shown in Figure 1.
- Change the name and use the drop down selections to select the type of server audits you would like to audit, as seen in Figure 2. (MSDN explanation of groups and actions)
- Right-click on the Server Audit Specification in the Security node and select enable to activate your new audit specification.
You can alternatively script this as well:
CREATE SERVER AUDIT SPECIFICATION [ChangingPermOwner]
FOR SERVER AUDIT [Audit-Test]
ADD (DATABASE_OBJECT_PERMISSION_CHANGE_GROUP),
ADD (DATABASE_OBJECT_OWNERSHIP_CHANGE_GROUP)
WITH (STATE = ON)
GO
Enjoy and stay tuned!
SQL Server Auditing: A Learning Series Part Four
Today we continue our series on Auditing with some clarifications. An audit is essentially the combination of several elements. This concept took a day or two to wrap around my brain so I thought I would discuss our way through it.
- The Audit Object is collected on either the server or database level. This covers actions as well as groups of actions.
- The Audit Specification is an object that belongs to an audit. This is a one-to-one relationship between audit object and audit specification. Both items are created at the instance level. The audit specification can collect many server-level or database-level action groups which are raised through extended events. You can have many groups within a specification. In addition, the audit specification is either a database or server specification and it cannot be both.
- The Audit Action Group is a predefined group of actions within the database engine itself. (See the MSDN list of Action Groups and Actions)
- The Target is essentially where the audit results are sent to, which we have already discussed as a file, the Application Log or the Security Log.
I hope this clarifies some points before we move forward. Enjoy and stay tuned.
SQL Server Auditing: A Learning Series Part Three
Continuing our learning series on Auditing, today we move on to setting up the server audit which will allow us to be able to setup auditing at the instance level.
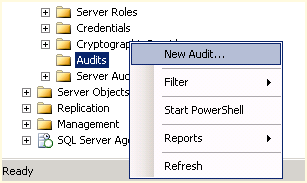
- In SSMS, open the Security node and right-click on Audits and choose New Audit as shown in Figure 1.
- This will present us with a default Create Audit dialog box as shown in Figure 2. Enter a name for your Audit being as descriptive as possible to make it easy for you to look back later and now what this is auditing.
- The Queue delay default is 1000 milliseconds. This is the delay before the audit actions will be processed.
- There is a check box if you would like to shut down the server when the audit log fails. In SQL Server 2012 you have the option to Continue, Shut down the server, or Fail the operation. Figure 2 is from a SQL Server 2008 server.
- As you can see in Figure 2, the default setting for the destination is the file and if this is the setting you choose then you must enter a file path in addition to the other settings shown. If you choose Security Log or Application Log then all of the file options will be unavailable.
- After this process is complete, you will see the audit named under Audits in the Security node. From there you need to right-click on it and select Enable Audit.
As with anything in the GUI SSMS, this too can be scripted as an example:
CREATE SERVER AUDIT [Test-Audit] TO SECURITY_LOG WITH (QUEUE_DELAY = 1000)
Enjoy and stay tuned.